Linux Users and Permissions
by Felix Kinaro About 2 min reading time
Overview
We explore the concept of users and permissions and their importance
User and Group Identifiers
- User ID - This is a unique integer assigned to every user to identify them to the Linux kernel. It determines what they can or cannot access.
- Group ID - Group identifier
How to find the UID and GID
sudo cat /etc/passwd
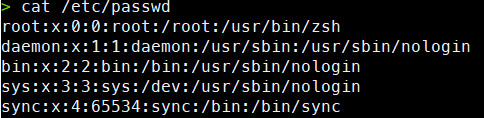
The columns are as follows:
- Column 1 – Name
- Column 2 – Password – If the user has set a password on this field, then it is indicated with the letter (x).
- Column 3 – UID (User ID)
- Column 4 – GID (Group ID)
- Column 5 – Gecos – Contain general information about the user and can be empty.
- Column 6 – Home directory
- Column 7 – Shell – The path to the default shell for the user.
Permissions
Permissions are divided into 4 categories of users:
- Owner
- Group
- Others
- All
There can be a combination of read (r), write (w) and execute (x). They can be assigned easily with the plus and minus signs to add or remove certain permissions. These modifications are done using the chmod command.
Binary references
We can use numbers as well to set the permissions of a file. Here is a simple table to demonstrate this.
- read: 4
- write: 2
- Execute: 1
- No permission: 0
For example we need to ensure that only I can view or modify my SSH keys directory. We can do this by running the following:
chmod 0600 ~/.ssh
This will deny all others the rights to view the contents. I on the other hand will be able to read (4) and write (2).
Ownership
The chown command is used to set the ownership of a file.
chown kinaro:kinaro text.txt
This sets the ownership of the file to user 'kinaro' and group 'kinaro' as well.
Other Attributes
- 'd' - Directory
- '_' - No special permissions
- 'l' - Symbolic link
- 's' - Setuid/setgid bit. Represented as a s in the read portion of the owner or group permissions.
Significance of permissions
- Restricting access to only the users that are allowed.
A good example is a user's home directory. We do not want other users viewing their files and making changes.
Another example would be configuration files. We don't want every user being able to modify bootloader, firewall and system files.