Disk Encryption
by Felix Kinaro About 2 min reading time
Disk encryption aims at keeping your private data secure against snoops.
You supply a password or keyfile, and using a ciphering algorithm, the data is encrypted.
Once the process is complete, you have to supply the password or keyfile you used in order to access the data.
The obvious downside to this is that you if you do not have a sound key recovery mechanism in case of lost keys, then you are locked out of the system.
We are going to look at 2 major forms of encryption:
- Disk encryption
- Encrypted containers
Disk Encryption
This works by encrypting a whole disk drive (Full disk encryption) or encrypting specific partitions.
The most popular tool for Windows systems is BitLocker. It is available to both Home and Pro users for Windows 10.
Bitlocker supports encrypting whole disks as well as specific partitions.
Find detailed instructions for Bitlocker on HowToGeek
You can also use VeraCrypt to encrypt entire disks, specific partitions or to create encrypted containers. VeraCrypt is Free and Open Source Software developed as a fork of
Full disk encryption using VeraCrypt
Go to VeraCrypt [Downloads] page and select an installer for your system.
Once you have installed the correct package for your system, open up VeraCrypt using the desktop shortcut icon or menu entry. Once the program starts you will have an interface similar to this image, except for the dark theme.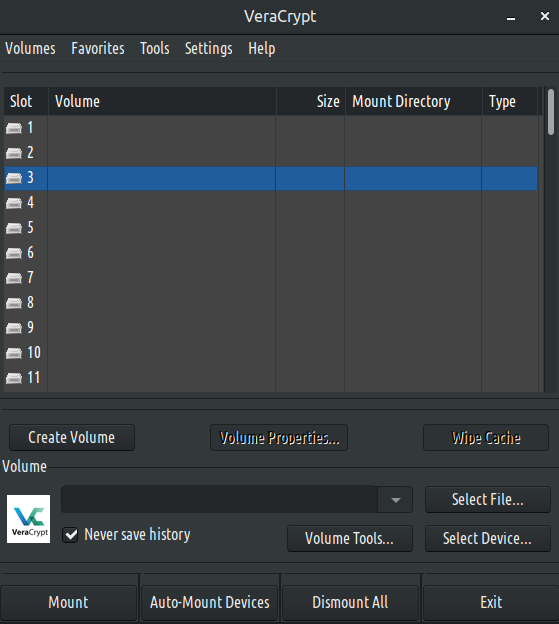
Click the Create Volume button. You have a choice between an encrypted container or encrypting an entire drive/partition.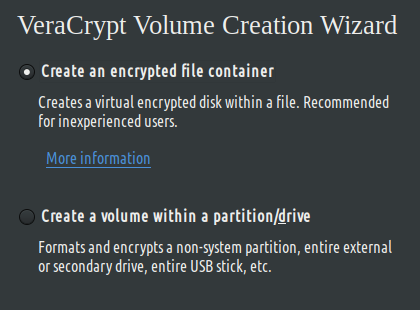
An encrypted file container resides on your computer's hard drive just like any other file. You can copy, move, share or delete it. Going further on creating encrypted containers, VeraCrypt also allows you to create a hidden volume. This is ideal for cases where you might be compelled, legally or otherwise, to provide your password.
The second option is to create an encrypted volume, which can be a normal volume or a hidden volume. A hidden volume allows you to install your OS within an encrypted volume. A malicious actor cannot differentiate between the outer and inner volume since any free space on either volume is filled with random data.
The most important requirement in all this is to use strong, random, unique passwords for each volume created.
Benefits of FDE
- There's of course the obvious benefit of confidentiality, even if you lose your laptop.
Downsides
- Support for GPT is currently unavailable. VeraCrypt can only encrypt system drives / partitions initialized with the MBR partition style.
- Complicated data recovery in the event of drive failure. It is always prudent to have backups.
- VeraCrypt asks you to burn an ISO image you can use to unlock your volume if you lose your password or keyfile. If you lose this disc you're in quite a mess.
- Slower boot time. Every time you power up you device, VeraCrypt will decrypt the files needed to boot your machine on the fly, hence introducing I/O overhead.
- Depending on the version you use, VeraCrypt may not automatically restore the original Master Boot Record. To fix this, you need a Windows DVD or bootable flash drive.
- Boot the flash drive/DVD
- Press SHIFT + F10 to open a command prompt window.
- Type bootrec /fixmbr. This will in most cases restore the original bootloader.
- Eject the flash drive / DVD and restart your computer. If everything went well, it will boot correctly