Password Brute Force Attack
by Felix Kinaro About 1 min reading time
In a password brute force attack, a hacker attempts all possible usernames and passwords to gain illegal access into a system. The process is carried out using automated software tools. The most commonly attacked service is SSH which runs on port 22 on a server. The Arch Linux wiki has an excellent tutorial on configuring SSH
One can easily identify brute force attacks in Linux. The first identifier is multiple attempts from the same IP address. I have an Ubuntu server where I have disabled SSH password log in, because I only use keys. Keys are superior over passwords since they are not vulnerable to brute force attacks.
Viewing failed login attempts on Linux
- Run
sudo lastbusing a non-root user account with sudo privileges.
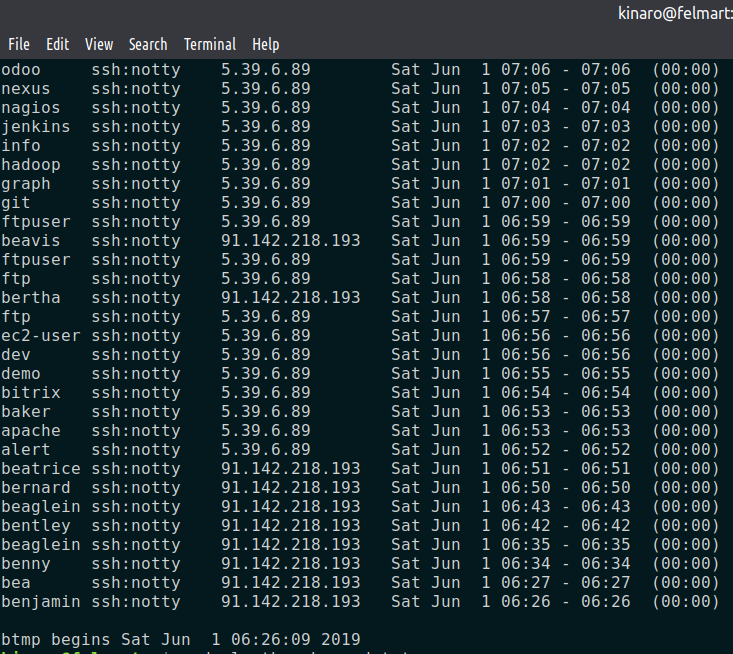
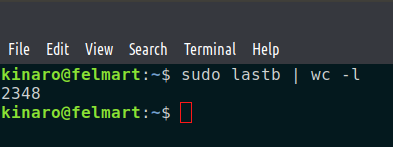
- To get the total number of failed attempts, pipe the output to the wc tool and pass the -l parameter to get the line count.
sudo lastb | wc -l
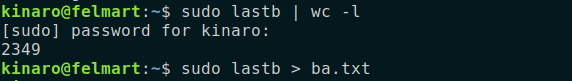
- To save the data to a text file:
sudo lastb > file.txt where file.txt is the name of the file. '>' directs the output of a command to a file.
You can then use the whois tool to get the details of a particular IP address if you wish. Install it using sudo apt install whois Consider using fail2ban to secure your server further.
Security should always be the first consideration whenever you deploy a product or service.